如何识别汽车机油泄漏
Visual Inspection Basics
Visual inspection is often the first and easiest step in identifying a car oil leak. This involves a careful, systematic examination of the engine bay and undercarriage. Look for any obvious signs of oil, such as puddles, streaks, or oily residue on surfaces. Pay close attention to areas around the engine, oil pan, valve cover gaskets, and oil filter housing. A thorough visual check can often pinpoint the general location of the leak, allowing for more focused troubleshooting later on.
Begin by warming up the engine slightly, as this will allow any potential leaks to be more readily apparent. Use natural light or a flashlight to illuminate areas under the vehicle and around critical engine components. Document your findings, noting the specific location and appearance of any suspected oil. A photograph or diagram can be invaluable in later diagnostics, especially if the leak is subtle or intermittent.
Identifying Common Leak Locations
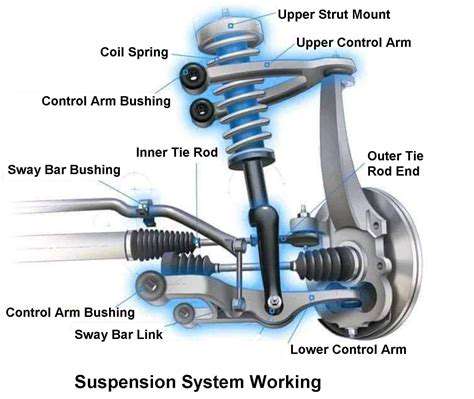
Certain areas of the car are more prone to oil leaks than others. Understanding these common leak locations will aid in your visual inspection. Oil pan leaks are frequently encountered due to the pan's position and its vulnerability to impacts or wear. The valve cover gasket is another common culprit, often revealing itself with oil around the valve cover and on the engine's upper components. Pay attention to the oil filter housing. Leaks here can be less obvious but can still result in a significant loss of oil over time.
Additionally, look for drips or stains around the oil dipstick area. This could indicate a leak from the dipstick tube itself, or a more extensive problem with the engine's internal seals. Inspect the area around the transmission or other fluid-carrying components. While not always oil, the presence of fluids of different colors or viscosities can help determine the type of leakage.
Tools and Techniques for Enhanced Visual Inspection
Using the right tools and techniques can significantly improve the effectiveness of your visual inspection. A high-quality flashlight with a strong beam is essential for illuminating hard-to-reach areas. Consider using a spray bottle with a lubricant-resistant cleaner to thoroughly clean the affected areas. This can help you better discern oil stains from other contaminants. A microfiber cloth or paper towels can be used to wipe away excess oil or debris, making it easier to spot any remaining traces of leakage.
Using a mirror or a borescope can also be helpful for looking into tight spaces or under the engine. A borescope, a small, flexible camera, is particularly useful for examining hard-to-reach areas and capturing detailed images of the suspected leak source. Take your time, and remember to focus on the details. Even small drips or smears can be indicative of a larger issue.

Pinpointing the Source: Tracking Down the Leak
Pinpointing the Source of Data Leaks
Data breaches are a significant concern in today's digital landscape, and understanding where these leaks originate is crucial for effective mitigation strategies. Identifying the specific entry points is often the first step towards preventing future incidents. Analyzing network traffic, user access logs, and system configurations can help pinpoint vulnerabilities and weaknesses, ultimately leading to a more secure environment for sensitive information.
Understanding the Data Leak Vectors
Data leaks can stem from a variety of vectors, each with its own unique characteristics and potential impact. For example, malicious actors often exploit vulnerabilities in software or hardware to gain unauthorized access. Poorly secured databases, exposed APIs, and insufficient user authentication practices also contribute significantly to data breaches.
The Role of Human Error in Data Leaks
While malicious intent plays a significant role, human error is frequently a contributing factor in data breaches. A misplaced email attachment, a compromised password, or insufficient security awareness training can all open doors for attackers to exploit. This highlights the importance of robust employee training programs and clear security protocols.
Technical Vulnerabilities as a Source
Technical vulnerabilities within software and hardware systems are often exploited by attackers to gain access to sensitive data. These vulnerabilities can range from outdated operating systems to misconfigurations in web applications. Addressing these technical vulnerabilities through regular security audits and updates is crucial for maintaining a strong security posture. Patching known vulnerabilities promptly is essential.
The Importance of External Threat Analysis
Data leaks are not always the result of internal weaknesses; external threats also play a significant role. Attacks from malicious actors, phishing campaigns, and denial-of-service attacks can compromise data security. Thorough external threat analysis is essential to identify potential threats and develop proactive countermeasures. Understanding the tactics and techniques used by attackers is critical.
Investigative Strategies for Pinpointing the Source
Investigative techniques are essential for determining the root cause of a data breach. This typically involves meticulously analyzing logs, examining system configurations, and interviewing personnel involved. A forensic approach is often necessary to reconstruct the events leading up to the breach, enabling the identification of the specific entry point and the responsible parties. This process can be complex and require specialized expertise.
Preventing Future Data Leaks
Once the source of a data breach has been identified, implementing preventative measures is crucial. This includes strengthening security protocols, enhancing user training, and implementing robust security controls. By learning from past incidents and implementing proactive security measures, organizations can significantly reduce the risk of future data leaks. Regular security assessments and vulnerability scans are vital for proactive identification of potential vulnerabilities.